Final goal: Drupal Web portal with TinyMCE JavaScript editor, Unicode and Locales support running on OpenBSD 4.3.
a. You can install OpenBSD via cdrom (install43.iso or cd43.iso for netinstall) or netboot via TFTP / BOOTP / DHCPD. Read diskless(8) for details. On Windows, you can use TFTPD32 for DHCP/TFTP.
b. Partition the disk (read the FAQ on partitioning). Example partitioning scheme:
| Partition | Mount location | Filesystem | Mount options | |
| /dev/sd0a | / | ffs | rw,softdep | 1 1 |
| /dev/sd0b | swap | swap | | |
| /dev/sd0c | Whole disk | | | |
| /dev/sd0d | /tmp | ffs | rw,softdep,nodev,nosuid | 1 2 |
| /dev/sd0e | /var | ffs | rw,softdep,nodev,nosuid | 1 2 |
| /dev/sd0f | /usr | ffs | rw,softdep,nodev | 1 2 |
| /dev/sd0g | /home | ffs | rw,softdep,nodev,nosuid | 1 2 |
c. Disable non-critical services (like ident, time, daytime, etc.) from /etc/inetd.conf. Just comment out the lines you don’t want with a #.
d. Make sure you enable Soft Updates (softdep) mounts – they increase the Filesystem performance tenfold when it comes to writing a lot of small files. This is done by adding “softdep” to mount options in /etc/fstab.
e. Add a regular user account. You can use the useradd(8) script. Make sure you add the user to the wheel group to allow su – root.
f. For added security configure „sudo” by running visudo(8). You can permit all users in the wheel group to sudo root: %wheel ALL=(ALL) NOPASSWD: SETENV: ALL
i. It’s usually best to disable root logins and use “sudo” for root access (sudo –i or su – if you need a root sheel). Edit /etc/ssh/sshd_config. You can also change the default ssh port from 22 to some random port to mitigate against brute force attacks. Keeps them from filling out your logs with junk. Consider using ssh keys also.
ii. Port 6969
iii. PermitRootLogin no
iv. Restart the OpenSSH daemon: „pkill –HUP sshd”
g. Configure your user profile to use a ftp mirror. Add the following to your ~/.profile: (or whatever shell you’re using, eg: .bashrc, .zshrc): PKG_PATH=ftp://ftp.su.se/pub/OpenBSD/4.3/packages/i386/; export PKG_PATH
h. Restart the system (to mount softdep, etc.).
i. Install some “critical” packages:
i. pkg_add -vi mc zsh screen elinks zip unzip bzip2
j. Install ports
i. cd /usr
sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/ports.tar.gz
sudo tar zxf ports.tar.gz
k. Unpack the OpenBSD source code (src and kernel – sys) – these are required for patching OpenBSD:
i. cd /usr/src
sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/src.tar.gz
sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/sys.tar.gz
sudo tar zxvf src.tar.gz
sudo tar zxvf sys.tar.gz
l. Apply OpenBSD security patches. You download patches from http://www.openbsd.org/errata43.html and you apply them using the instructions in the patch headers:
i. ftp ftp://ftp.openbsd.org/pub/OpenBSD/patches/4.3.tar.gz
You can put 001_openssh.patch, 002_openssh2.patch and the following patches in /usr/src and apply them. Read the header for the patches for instructions.
% head -11 001_openssh.patch
Apply by doing:
cd /usr/src
patch -p0 < install ="="> lib
===> ssh
install -c -s -o root -g bin -m 555 ssh /usr/bin/ssh
install -c -o root -g bin -m 444 ssh.cat1 /usr/share/man/cat1/ssh.0
install -c -o root -g bin -m 444 ssh_config.cat5 /usr/share/man/cat5/ssh_config.0
/usr/share/man/cat1/slogin.0 -> /usr/share/man/cat1/ssh.0
/usr/bin/slogin -> /usr/bin/ssh
===> sshd
install -c -s -o root -g bin -m 555 sshd /usr/sbin/sshd
install -c -o root -g bin -m 444 sshd.cat8 /usr/share/man/cat8/sshd.0
install -c -o root -g bin -m 444 sshd_config.cat5 /usr/share/man/cat5/sshd_config.0
===> ssh-add
install -c -s -o root -g bin -m 555 ssh-add /usr/bin/ssh-add
install -c -o root -g bin -m 444 ssh-add.cat1 /usr/share/man/cat1/ssh-add.0
===> ssh-keygen
install -c -s -o root -g bin -m 555 ssh-keygen /usr/bin/ssh-keygen
install -c -o root -g bin -m 444 ssh-keygen.cat1 /usr/share/man/cat1/ssh-keygen.0
===> ssh-agent
install -c -s -o root -g _sshagnt -m 2555 ssh-agent /usr/bin/ssh-agent
install -c -o root -g bin -m 444 ssh-agent.cat1 /usr/share/man/cat1/ssh-agent.0
===> scp
install -c -s -o root -g bin -m 555 scp /usr/bin/scp
install -c -o root -g bin -m 444 scp.cat1 /usr/share/man/cat1/scp.0
===> sftp-server
install -c -s -o root -g bin -m 555 sftp-server /usr/libexec/sftp-server
install -c -o root -g bin -m 444 sftp-server.cat8 /usr/share/man/cat8/sftp-server.0
===> ssh-keysign
install -c -s -o root -g bin -m 4555 ssh-keysign /usr/libexec/ssh-keysign
install -c -o root -g bin -m 444 ssh-keysign.cat8 /usr/share/man/cat8/ssh-keysign.0
===> ssh-keyscan
install -c -s -o root -g bin -m 555 ssh-keyscan /usr/bin/ssh-keyscan
install -c -o root -g bin -m 444 ssh-keyscan.cat1 /usr/share/man/cat1/ssh-keyscan.0
===> sftp
install -c -s -o root -g bin -m 555 sftp /usr/bin/sftp
install -c -o root -g bin -m 444 sftp.cat1 /usr/share/man/cat1/sftp.0
===> scard
install -c -m 444 -o root -g bin Ssh.bin /usr/libdata/ssh
- 2. Restart the system to apply patches (or just the affected services by using pkill –HUP for example if you didn’t patch the kernel).
a. % cd / && sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/i386/xbase43.tgz
% sudo tar xzvphf xbase43.tgz
a. % sudo pkg_add -vi php5-core php5-mysql php5-curl php5-mbstring php5-gd
Ambiguous: choose package for php5-gd
0:
1: php5-gd-5.2.5
2: php5-gd-5.2.5-no_x11
Your choice: 1
parsing php5-gd-5.2.5
b. Activate PHP modules by creating the various symbolic links:
i. % sudo ln -s /var/www/conf/modules.sample/php5.conf /var/www/conf/modules
ii. % sudo ln -fs /var/www/conf/php5.sample/curl.ini /var/www/conf/php5/curl.ini
iii. % sudo ln -fs /var/www/conf/php5.sample/gd.ini /var/www/conf/php5/gd.ini
iv. % sudo ln -fs /var/www/conf/php5.sample/mbstring.ini /var/www/conf/php5/mbstring.ini
v. % sudo ln -fs /var/www/conf/php5.sample/mysql.ini /var/www/conf/php5/mysql.ini
5. Install, configure and secure the MySQL database:a. % sudo pkg_add -vi mysql-server
b. Installing the default database
i. % sudo /usr/local/bin/mysql_install_db
c. Starting the MySQL service:
i. % sudo /usr/local/bin/mysqld_safe&
[1] 32390
% Starting mysqld daemon with databases from /var/mysql
d. Secure the installation (delete anonymous users, the test database and set a root password). PS: don’t use # in your password, there’s a bug in the script. Set that manually if you want.
i. % sudo /usr/local/bin/mysql_secure_installation
e. Tune some sysctl parameters for MySQL:
i. Edit /etc/sysctl.conf:
kern.shminfo.shmall=32768
kern.maxfiles=8192
ii. Apply the changes
% sudo sysctl kern.shminfo.shmall=32768
kern.shminfo.shmall: 8192 -> 32768
% sudo sysctl kern.maxfiles=8192
kern.maxfiles: 3580 -> 8192
iii. Add a mysql login in /etc/login.conf:
mysql:\
:openfiles-cur=1536:\
:openfiles-max=3096:\
:tc=daemon:
iv. % sudo cap_mkdb /etc/login.conf
6. Configure SSL (Secure Sockets Layer) for Apache mod_ssl (https). Generate a self signed certificate (or sign one) by reading ssl(8).a. % sudo openssl genrsa -out /etc/ssl/private/server.key 1024
% sudo openssl req -new -key /etc/ssl/private/server.key -out /etc/ssl/private/server.csr
% sudo openssl x509 -req -days 365 -in /etc/ssl/private/server.csr -signkey /etc/ssl/private/server.key -out /etc/ssl/server.crt
b. Test SSL support (lynx is ssl enabled):
% sudo apachectl startssl
% lynx https://localhost
a. Edit the Apache configuration file and setup PHP and server details /var/www/conf/httpd.conf
AddType application/x-httpd-php .php
ServerAdmin cmihai@website
DirectoryIndex index.html index.php
ServerName hostname(fqdn)
b. Configure PHP:
i. Edit the PHP config /var/www/conf/php.ini
upload_max_filesize = 12M
c. Test PHP:
ed /var/www/htdocs/index.php
a
Test PHP:
.
w
q
% lynx http://localhost/index.php
d. Configure Sendmail for supporting the Apache chroot[1]
% sudo pkg_add -vi mini_sendmail-chroot
parsing mini_sendmail-chroot-1.3.6p0
mini_sendmail-chroot-1.3.6p0: complete
% sudo mkdir -p /var/www/usr/sbin/
% sudo ln /var/www/bin/mini_sendmail /var/www/usr/sbin/sendmail
% sudo cp /bin/sh /var/www/bin
a. % sudo ed /etc/rc.conf
httpd_flags="-DSSL"
b. % sudo ed /etc/rc.local
if [ -x /usr/local/bin/mysqld_safe ] ; then
su -c mysql root -c '/usr/local/bin/mysqld_safe >/dev/null 2>&1 &'
echo -n ' mysql'
fi
# Crearea unui link pentru socketul MySQL in chrootul Apache
mkdir -p /var/www/var/run/mysql
sleep 5
ln -f /var/run/mysql/mysql.sock /var/www/var/run/mysql/mysql.sock
c. Reboot to test changes.
9. Crate a database for Drupal and a user. Grand permissions:a. % sudo mysql -u root -p
CREATE USER drupal IDENTIFIED BY 'password';
CREATE DATABASE drupal CHARACTER SET utf8;
GRANT ALL PRIVILEGES ON drupal.* to USER drupal@localhost IDENTIFIED BY 'password';
a. % sudo pkg_add -vi drupal5-tinymce drupal5-link-to-content drupal5-imce drupal5-image drupal5-backup-migrate drupal5-autolocale drupal5-token drupal5-securelogin ImageMagick
11.Optionally configure .httauth for security:a. % cd /var/www
% sudo htpasswd -c htpasswd username
Add .htaccess to /var/www/htdocs
AuthName "Nu este permis accesul"
AuthType Basic
AuthUserFile ../htpasswd
require valid-user
b. Add “Add AllowOverride All” în /var/www/conf/httpd.conf.
c. Restart Apache (apachectl stop && apachectl startssl).
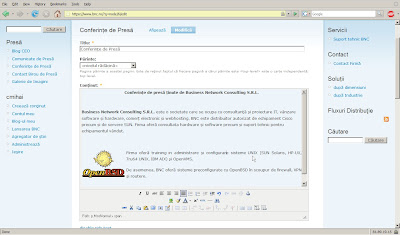
You can now configure Drupal and the various modules. Be sure to setup a backup schedule. You can use the Drupal database backup and restore module.
You can also install Apache mod_security for additional security:
% sudo pkg_add -vi modsecurity-apache
% sudo /usr/local/sbin/mod_security-enable
% sudo apachectl stop && sudo apachectl startssl
Make sure you read /usr/local/share/doc/mod_security/modsecurity-manual.pdf
You should also keep an eye on your webserver. For monitoring, I recommend top(1), vmstat, (8), sysctl hw, pftop and mytop.
% sudo pkg_add -vi mytop pftop
% sudo /usr/local/sbin/pftop
To use mytop you'll need a ~/.mytop file (and set proper permissions on it). You can add something like:
prompt=1
pass=
user=drupal
db=drupal
delay=5
port=3306
socket=
batchmode=0
header=1
color=1
idle=1
% mytop
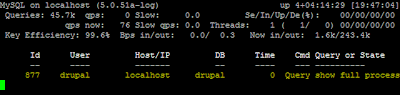
MyTOP in Action
You'll also want to setup Packet Filter. Read the PF User's Guide, pf.conf(5) and the example rulesets in /usr/share/pf/examples. Enable pf in /etc/rc.conf (pf=YES).
[1] Read chroot(2) ssl(8) afterboot(8), etc.


3 comments:
Heh, sorry about the botched html, blogger does make things messy when trying to paste code. Anyway, for testing and stuff anyone should already be pretty familiar with phpinfo();
http://www.php.net/phpinfo
Use:
GRANT ALL PRIVILEGES ON drupal.* to 'drupal'@'localhost' IDENTIFIED BY 'password';
Also, drupal6 packages are available now with OpenBSD 4.6. FCKEditor can replace TinyMCE.
I want to install OpenBSD. thanks are guided on how to install
Post a Comment