Here are a few quick steps for performing malware analysis on various badware (viruses, works, trojans, rootkits) that you may find in the course of a computer forensics investigation. In this case, I'm analyzing a variant of Sohanad, a Instant Messaging Worm, also known as "the cool pics worm".
Tools of the trade:
- Virtualization
- VirtualBox - it's free, open source and multi-platform (Windows, Linux).
- VMware Server (Linux, Windows), free
- qemu - available on multiple platforms (Windows, Linux, BSD, UNIX), free, open source
- Microsoft VirtualServer / VirtualPC
- File analysis
- File Analyzer
- PE Explorer
- PEiD detects most common packers, cryptors and PE compilers (over 470 signatures).
- Debuggers, disassemblers
- OllyDBG
- Ida Pro Freeware
- Immunity Debugger
- Hex Editors
- File Alteration Monitors
- Sysinternals ProcMon, FileMon, RegMon, Process Explorer
- Network Monitors
- Wireshark (aka Ethereal)
- Windows Network Monitor
- Rootkit revealers, startup listers
- Tools
- Antivirus
- Virustotal - Analyzes uploaded files using over 33 Anti-Virus engines.
- Virus.org - Scans uploaded files with over 20 Anti-Virus engines (some differ from virustotal). It's interesting to see how many Antivirus products fail to spot a virus.
- Viruslist - Information about Viruses
- VirusPool - Malware Research Database
- Documentation
- PECOFF - Microsoft Portable Executable and Common Object File Format Specification
Initial configuration of the workbench:
We're going to setup VirtualBox (or any other virtualization product) with a copy of Windows XP SP2, update it and take a snapshot so we can easily move back to a clean system.
- Use VirtualBox to install WindowsXP SP2 in a Virtual Machine.
-
Take a snapshot of the Virtual Machine - Initial Install.
-
Install VirtualBox Guest Additions
- Install Microsoft Update and update the system.
- Create an ISO image of your tools, and mount it inside the Virtual Machine.
- Take another snapshot of the Virtual machine - Updated and configured.
- Add your tools to PATH to speed things UP.
Analyze the malware:
- Use Process Explorer, Sysinternals Autoruns, RootKitRevealer, HiJackThis and so on to find running processes and targets for analysis, then put them in the virtual machine "sandbox". Also, make sure you check the Digital Signature for files you may suspect of being malware (Right Click - Properties - Digital Signatures). A good way of revealing malware is looking for suspicious entries in Sysinternals Autoruns (just hide signed Microsoft Entries, then look for Unsigned or Fake signature entries). Remember though, malware can also be digitally self-signed.
- The Target: "New Folder.exe" - self described as "Worm2007" by "IT University".
- Determine file type using "magic": file "New Folder.exe", PeID and File Analyzer to get headers info.
- Use "strings" to parse the file for Unicode and ASCII strings: strings -n 8 "New Folder.exe"
- Use "head " to see the first few lines of the file: head -5 "New Folder.exe" - We can already see this file is packed using UPX. upx -l "New Folder.exe" confirms this.
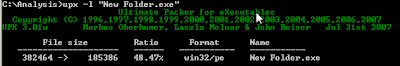
- Uncompress the file: upx -d "New Folder.exe"
- Parse the file again with "file" and "strings" - this time we can see a lot more information.
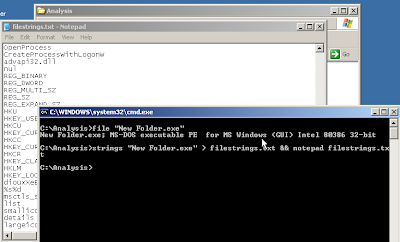
- Use PE Explorer and "File Analyzer" to get even more information about PE Headers, dependencies and so on.
- Fire up OllyDbg, IDA Pro Freeware, Immunity Debugger, WinDBG or your favourite debugger / disassembler and analyze the file.
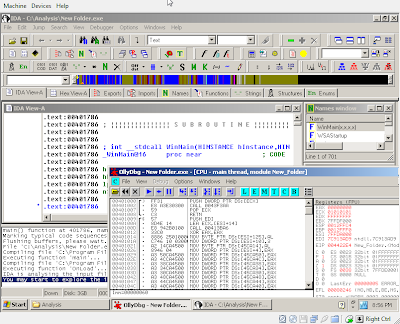
- Start Sysinternals ProcExp (Process Explorer - taskman on steroids), ProcMon (filemon and regmon combined), handle (check file handles) and TCPView and Wireshark (aka Ethereal) or MS Network Monitor, and run the piece of malware! We're going to see exactly what files and registry items it tries to change, what network connections it opens and what kind of network traffic it generates. We can also use "netstat -abn" to list network connections. We can later just restore the VirtualBox snapshot to get back to an untainted system.
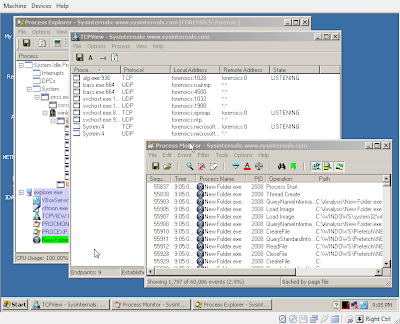
- We restart the machine to allow the malware to apply it's group policies and registry changes / autoruns properly :-). We can see the effect of the applied group policies (disables regedit and taskman, but forgets about gpedit.msc and tasklist for example).
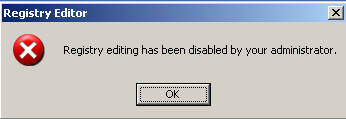
- We use Sysinternals Autoruns, RootKit Revealer and HiJack this to see how this piece of malware starts. With Sysinternals Autoruns we simply hide signed microsoft entries, and we can see 3rd party products, such as our piece of badware, hiding in lsass or svchost or ymessenger named entries.
- We use HiJack This to list changes to our system like disabling regedit, starting a really strange "svchost32.exe" that shouldn't be there and making the IE default webpage "thec**lpics.com" -> don't access it, it's the Malware's homepage…
O4 - HKLM\..\Run: [Task Manager] C:\WINDOWS\svchost32.exe
O6 - HKCU\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System, DisableRegedit=1
To remove the malware, you just need to reverse all the chances it has performed to the registry and filesystem. Once you've written down the location of the files from ProcMon and the running binaries from ProcExp, you can start by stopping the virus:
You can stop the Virus processes easily with Process Explorer, or you could just use "taskkill":
taskkill /F /IM svchost32.exe /TYou could also disable it from running at startup by removing it using Sysinternals Autoruns.
Once you've identified all the processes and what executables they were running from, just use WinDiff, EasyDuplicateFinder or something similar to find all identical binaries, and remove them.
You can the use "Fixed Checked" in HiJack this, and "reg add" or "reg delete", a .reg file or gpedit.msc to manually enable the Registry Editor or other disabled features in Windows. You could also use an offline Registry Editor. Example:
reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\" /v "DisableTaskMgr"To restore the missing files the malware removed (like msconfig.exe) just pop in the Windows cd, and use "expand" to uncompress and restore them: EXPAND -R D:\I386\MSCONFIG.EX_ c:\Windows\System32. Windows may also keep some copies of msconfig.exe around, but they may or may not be safe. Check the digital signature.
reg delete "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v "DisableRegistryTools"
reg delete "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v "DisableRegistryTools"
reg add "HKCU\SOFTWARE\Microsoft\Internet Explorer\Main" /v "Window Title" /d ""
reg add "HKCU\SOFTWARE\Microsoft\Internet Explorer\Main" /v "Start Page" /d "http://www.msn.com"