Number one reason you shouldn't paste your Cisco configs or password hashes on the Internet:
Cisco's PIX password encryption is a base64 encoded MD5 hashsum, using only one MD5 update (no salting or anything). This also permits for cryptanalysis attacks using rainbow tables to speed up the process.
Simple hashes like:
enable password RLPMUQ26KL4blgFN encrypted
Get cracked instantly. -> 1234

Also, note that MD5 has know weaknesses in the algorithm, that may allow for more complex password cracking attacks.
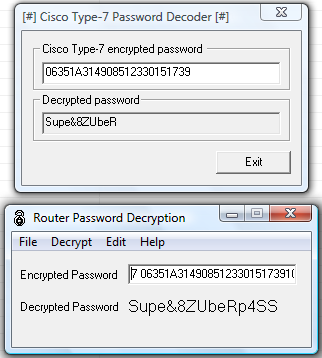
Also, if you're using a "type 7" password, that's pretty much useless, since it can get cracked instantly. People can just use simple tools such as Cain and Abel, or Solarwinds Router Password Decryption to reverse the crypto on type 7 passwords.
someuser privilege 0 password 7 06351A3149085123301517391C501918
IOS type 5 passwords (MD5 using 1000 rounds) is more complex, and harder to crack, but yous still shouldn't paste your hashes for everyone to see... Remember, even with type 5 passwords, you're still vulnerable to dictionary attacks, hybrid attacks, rainbow table attacks (PIX only), md5 repository attacks, or plain old password guessing.
If you're going to paste your config files anywhere, use the "show tech-support" command available in newer IOS versions. It gives more info, and strips confidential information, password hashes and such.
You can even use decrypt.pl - a neat little Perl script to instantly decrypt type 7 passwords:
#!/usr/bin/perl -w
# $Id: ios7decrypt.pl,v 1.1 1998/01/11 21:31:12 mesrik Exp $
#
# Credits for orginal code and description hobbit@avian.org,
# SPHiXe, .mudge et al. and for John Bashinski
# for Cisco IOS password encryption facts.
#
# Use for any malice or illegal purposes strictly prohibited!
#
@xlat = ( 0x64, 0x73, 0x66, 0x64, 0x3b, 0x6b, 0x66, 0x6f, 0x41,
0x2c, 0x2e, 0x69, 0x79, 0x65, 0x77, 0x72, 0x6b, 0x6c,
0x64, 0x4a, 0x4b, 0x44, 0x48, 0x53 , 0x55, 0x42 );
}
while (<>) {
if (/(password|md5)\s+7\s+([\da-f]+)/io) {
if (!(length($2) & 1)) {
$ep = $2; $dp = "";
($s, $e) = ($2 =~ /^(..)(.+)/o);
for ($i = 0; $i < length($e); $i+=2) {
$dp .= sprintf "%c",hex(substr($e,$i,2))^$xlat[$s++];
}
s/7\s+$ep/$dp/;
}
}
print;
}


0 comments:
Post a Comment